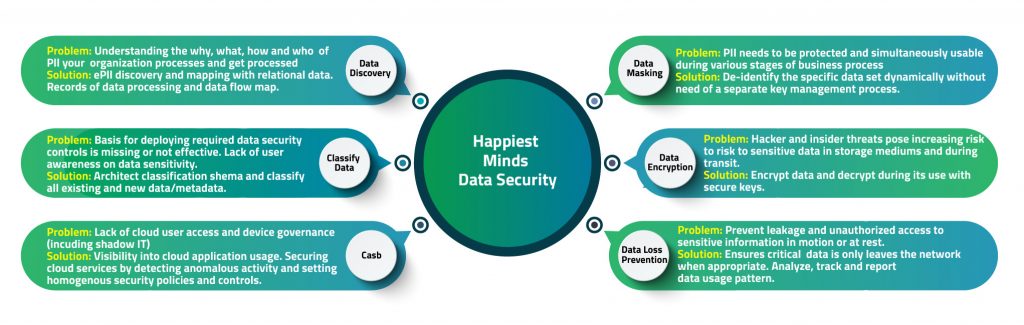
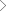Data security and privacy risks are becoming more prominent in the business fabric of small to large organizations today. Businesses across the globe are facing productivity loss and are running at higher data security risk. Current data protection methods are rendered obsolete due to incessant growth in data generation and usage across multiple data silos in an organization.
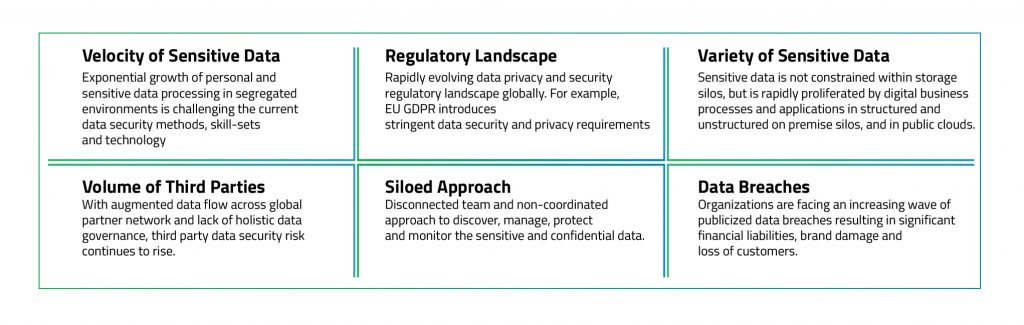
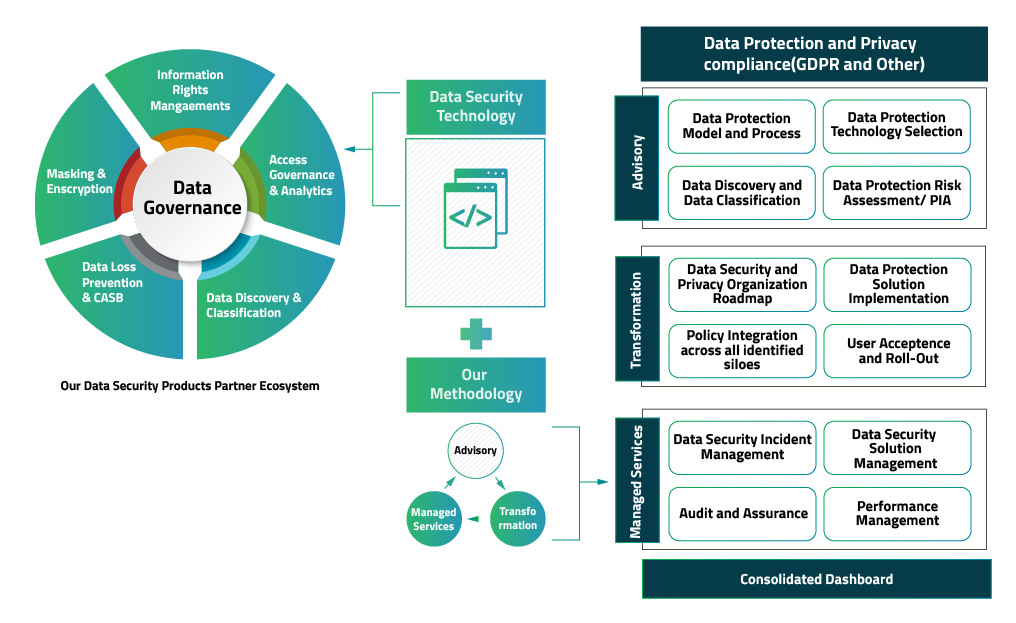
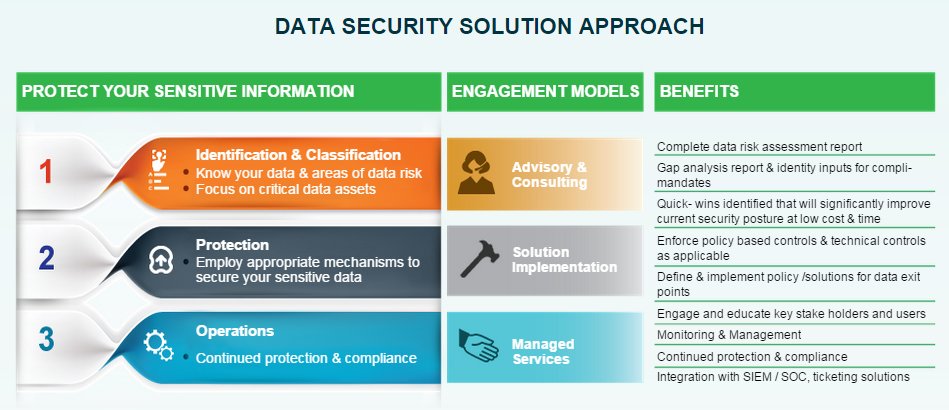
Our advisory based Data-Centric Security service offers holistic technology solution to secure sensitive data in your organization across creation, use and transmission.
Happiest Minds Data-Centric Security services incorporate a risk-based strategy with leading data protection solutions to protect your organization’s critical data across its lifecycle.