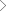Governance Risk and Compliance
In a volatile and dynamically changing business environment, risk management, and information assurance play a critical role in the overall growth and sustenance of any organisation. Due to the increasing dependence on digitally enhanced infrastructure, CIOs face the daunting challenge of striking the right balance between protection and progress as well as privacy and governance. Adding to the above dilemma, is a fragmented and, sometimes defocused, security posture resulting from a multi-regulatory mandate.
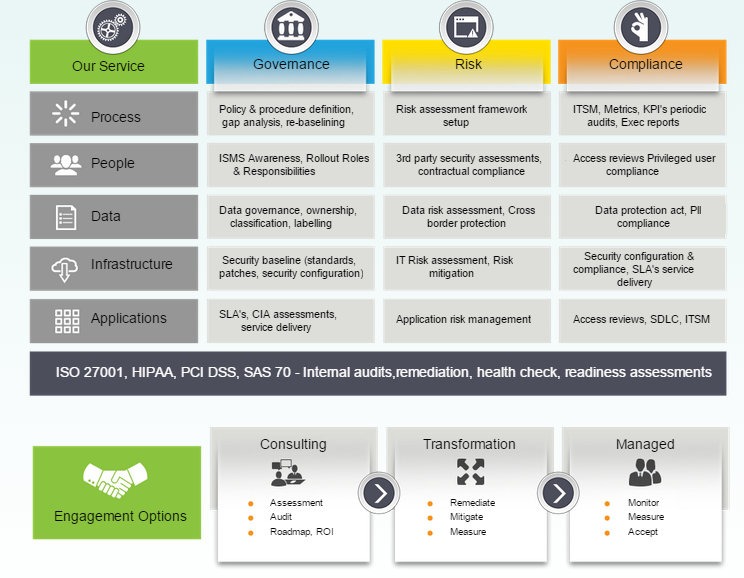
Therein lies the need for a holistic governance risk and compliance framework.
Governance Risk and Compliance Challenges
- Lack of visibility on critical data and crucial assets
- Impact and losses due to a breach or perceived threat
- Incomplete coverage of security controls and assets
- Optimization of governance risks and compliance management tools
- Visibility of current governance risk and compliance posture