Timely identification, assessment and management of security risks associated with business applications, networks, mobile devices and related technology environments enable enterprise stakeholders to address emerging threats while maintaining compliance with applicable regulations, legislative requirements and industry standards. Thus, proactive remediation of design flaws and IT security assurance in the business system is important to prevent customer lawsuits, legal penalties, regulatory fines and loss of reputation.
Organizations require best in class technology, robust processes and technical specialists to empower business owners to continuously innovate and focus on the core business without compromising on security. And that’s what makes IT security assurance imperative.
• Adherence to industry standards and frameworks
• Certified and highly skilled resources
• Security control assurance
• Reduced zero false positives
• Information protection
IT security assurance is the foundation enterprises need to build for determining trustworthiness of features, practices, processes, procedures and architecture of the information system. IT security assurance services assist clients across a wide range of industry verticals in determining the compliance level of the technical security controls with applicable regulations, legislative and standard requirements such as PCI DSS, UK DPA, HIPAA and ISO 27001.
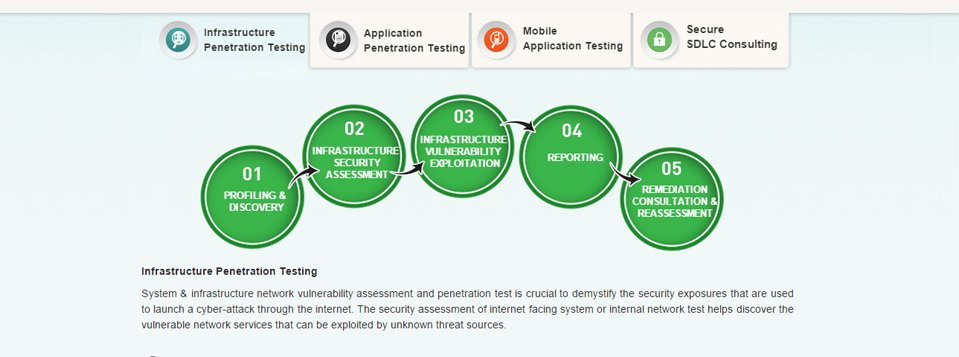
Technical security assessments comprise vulnerability assessments and penetration testing of all the system components that include business applications, databases, secure network perimeters, systems and network infrastructure, mobility solutions and virtualized cloud environments for global client base.