Quantum computing has long been discussed in scientific circles as a breakthrough technology, something that could solve certain problems far beyond the capabilities of today’s computers. But over time, it’s moved from theoretical buzz to a real-world consideration — especially in the world of cybersecurity. For many industries, it’s no longer about whether quantum computers will arrive, but when, and more importantly, what happens next.
Despite the hype, large-scale quantum computers capable of breaking encryption aren’t quite here yet. Even Nvidia’s CEO recently suggested we’re still about a decade away. That might sound comforting at first, but it masks a far more immediate issue — one that’s already impacting how we should think about securing the internet.
At the heart of that issue is encryption — specifically the encryption that secures nearly every transaction and piece of data that moves across the web.
What is the Real Risk?
Much of internet security today depends on encryption methods like Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC). These rely on mathematical problems like factoring large prime numbers (used in RSA) or calculating discrete logarithms (used in ECC). These techniques are almost impossible to break using classical computers and therefore widely used.
Quantum computers, on the other hand, operate differently and they are believed to solve certain problems dramatically faster. Specifically in the case of cryptography they have been shown to break the algorithms which are used in RSA and ECC. Algorithms like Shor’s and Grover’s algorithm, make quick work of what would take a classical computer thousands of years. That puts RSA and ECC, which are the primary ways in which we secure data, in serious danger.
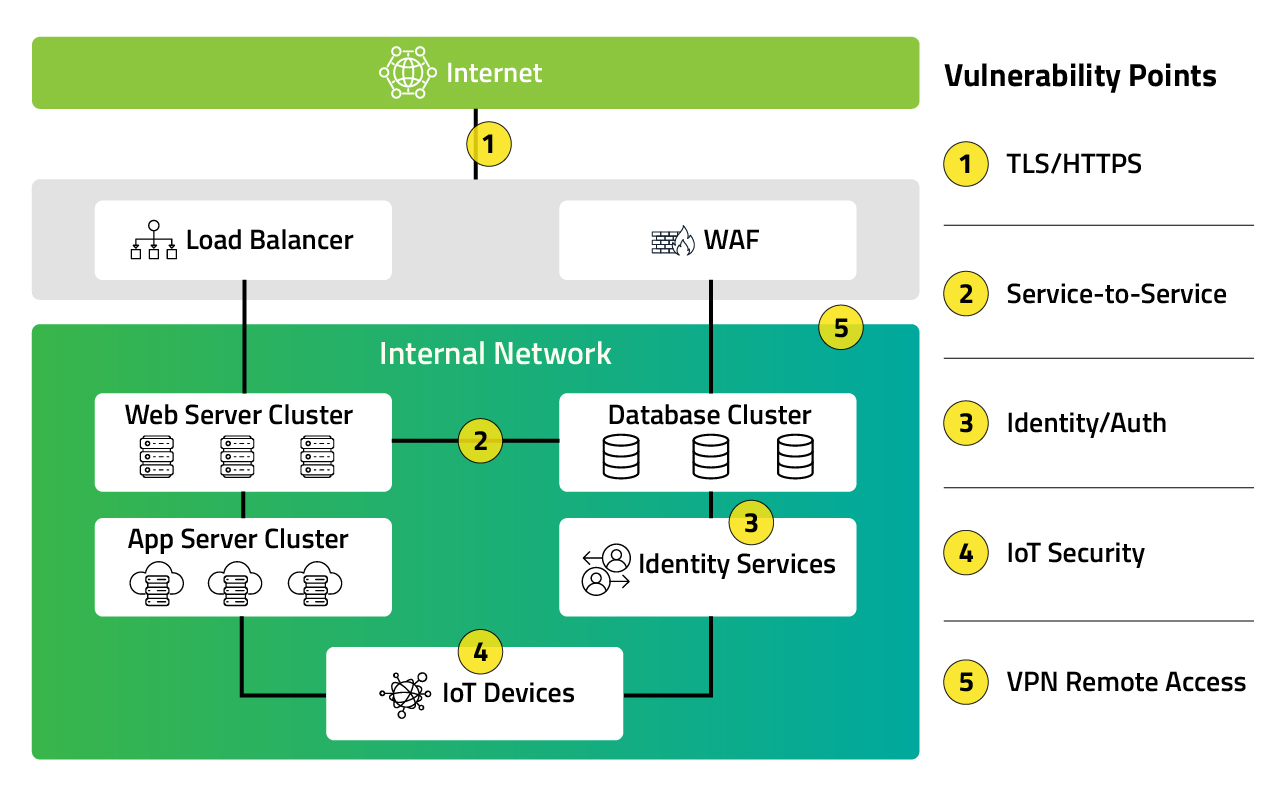
It’s not a theoretical threat anymore. The very infrastructure that powers the internet — from your browser to your banking app — is built on encryption that may not stand up to the quantum future.
Isn’t Quantum Still Years Away?
In terms of mass-market deployment? Yes, it probably is. But in terms of cybersecurity risk? The threat has already arrived.
There’s a tactic known as ‘Harvest Now, Decrypt Later’. Hackers are intercepting and storing encrypted data today, fully expecting to decrypt it once quantum computers become strong enough. So even if quantum computing is still years out, the danger to today’s data is very real.
Moreover, Transport Layer security (TLS), which uses RSA and ECC, is mostly used in IoT and Blockchains. As a result, there are widespread implications, and it wouldn’t be hyperbole to say that the whole internet is at risk.
Exploring Possible Solutions
Thankfully, researchers and security organizations like National Institute of Standards and Technology (NIST) and Cloud Security Alliance (CSA) have been working actively towards finding solutions which can be implemented to secure the internet.
1) Post-Quantum Cryptography (PQC)
PQC is a practical, software-based response to the quantum threat. It involves new cryptographic algorithms that are designed to be secure even against quantum computers. The National Institute of Standards and Technology (NIST) has been leading the charge in evaluating and standardizing these new methods.
In November 2024, NIST published Interagency Report (IR) 8547, which offered guidance for transitioning from today’s encryption to quantum-resistant alternatives. Some of these algorithms are already supported by popular tools:
– Browsers like Chrome and Firefox can handle PQC over TLS.
– The latest OpenSSL (3.5.2) comes with PQC cipher suite support.
– Many cloud and security vendors are beginning to roll out PQC-ready services.
2) Quantum Key Distribution (QKD)
QKD is another approach that uses quantum physics itself to securely share encryption keys. It’s cutting-edge and promising, but comes with certain trade-offs. You need specialized equipment and robust infrastructure to make it work — which makes widespread adoption a challenge, at least for now.
While QKD has its place, especially in high-security government or defense use cases, PQC offers a more immediate, scalable path for most organizations. NIST and most of the government agencies have suggested all enterprises like financial institutions and healthcare providers that have a lot of sensitive information should implement PQC. There are guidelines from NIST (IR 8547) and also from cloud providers like AWS and Azure on what enterprises can do to seamlessly adopt PQC.
Don’t Forget Internal Systems
One commonly overlooked area is internal service-to-service communication — especially in systems using microservices. Many teams assume these internal interactions are safe because they’re behind firewalls or inside secure VPCs. But if an attacker makes it past the edge, they often find little resistance moving between services.
That’s where mutual TLS (mTLS) comes in. And now, there’s growing interest in PQC-enabled mTLS, which not only keeps internal communication encrypted but also ensures it stands the test of time — including the quantum future.
Why Architects need to take this Seriously?
Architects should think about scalability, maintainability, and security — not just for today, but for the long run. With the quantum era approaching, we must start building systems that can evolve as encryption standards change.
Ask yourself:
– Are we using cryptographic tools that can evolve with the standards?
– Can our systems adapt quickly when new encryption methods become the norm?
– Are we securing internal traffic with the same seriousness as external APIs?
A few steps to consider:
– Use abstraction to decouple encryption logic from application logic.
– Adopt libraries that support hybrid encryption and PQC-friendly standards.
– Plan for regular certificate rotation and future-proof mTLS implementations.
What are Tech Leaders doing?
Big tech companies like Google are already investing heavily in PQC. From DNS resolution to TLS handshakes, they’re ensuring that their infrastructure is quantum-ready — not just in theory, but in deployment. AWS has provided options to use PQC to interact with KMS and other services.
Our Perspective at Happiest Minds
At Happiest Minds, we see the quantum threat not as a distant problem but as a current architectural challenge — and an opportunity.
We’re actively investing in:
– Reference implementations that make it easier to adopt PQC in cloud-native and enterprise systems.
– Design frameworks that help businesses migrate without needing to overhaul their existing setups.
– Tools and accelerators for integrating PQC into microservices, APIs, and internal communications.
We will actively work with our customers in banking, healthcare, public services and connected devices to ensure they are sensitized about impending threat and the effectiveness of existing solutions. Our philosophy is to help our clients in choosing solutions that generate the least friction and can be seamlessly implemented without disrupting regular business operations. We understand the criticality of helping our customers in building the essential guard rails and safety mechanisms to ensure their platforms are robust, secure and future-ready.
If you’re designing or maintaining platforms with long-term data sensitivity — in banking, healthcare, IoT, or public services — now is the time to start incorporating PQC.

He is the Chief Architect – Product and Digital Engineering Services at Happiest Minds Technologies, with over 25 years of IT experience. He combines deep technical expertise with a passion for solving real business challenges. He has worked across diverse industries—healthcare, banking, insurance, edtech, and automotive—with a strong grasp of domain-specific needs and solution-oriented delivery.
He has built secure, scalable, and sustainable systems using a range of technologies and SaaS platforms. His expertise spans cloud computing, IoT, machine learning, and quantum computing. Known for simplifying complex technologies into practical, value-driven solutions, he has played a key role in delivering tangible business outcomes.




