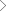Organizations are now leveraging cloud-based models to adopt security services and solutions. This shift has occurred for a variety of reasons. With cloud-based security, you eliminate the cost and hassle of provisioning, managing, scaling security hardware and software, ensuring fast, consistent delivery of the newest security technologies & updates, helping you stay compliant and thereby reduce risk.
Happiest Minds offers comprehensive Integrated Security-as-a-Service (iSaaS) solutions covering compliance management, identity and access governance, Cyber security and application & mobile security through its home grown IPs namely ComplianceVigil, IdentityVigil, CyberVigil and ThreatVigil.
The integrated Vigil platforms provide best of both the worlds in terms of technology, tools, and industry standard processes & services bundled together at a cost which is affordable, providing a compelling value proposition for a customer to consider.
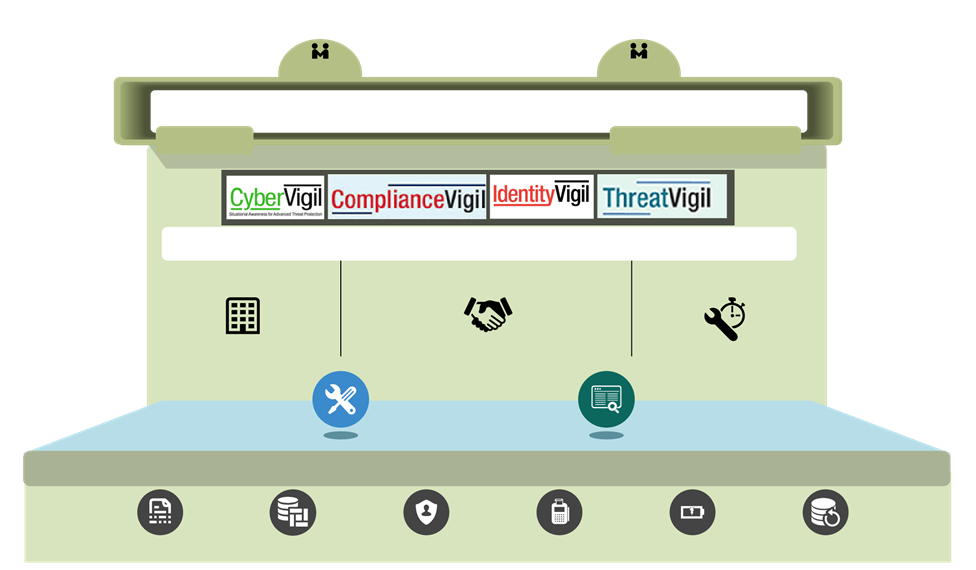
Partner
Consumer
Self service
Service Management
Management Portal
Happiest mind’s smart security frame work
Security service factory
Business Enablement
Service Management
- Service Catalog,SLA
- Service Automation
- Business Case Identification
- Cloud Service Migration
- 24*7 Support(Std/Patd)
- Training (online/Offline)
Framework for customization & Application Business logic
Virtualization
Resource Management
Security
Billing
Charging
Backup
WHY iSaaS
- Existing on-premise solutions for Compliance Management, Access Governance, Threat Management and Cyber Security have been designed, marketed & sold with high infrastructure & deployment costs. There is also a lack of skilled resources to build and manage challenges in customization and integration with custom applications and systems
- The traditional enterprise security model is reactive and often entails significant latency between the time a security event is discovered and when protection is made available resulting in significant gaps in security coverage
- A large on-premise rollout can take several months, and often requires complex project management and lots of resources.
Features & Benefits
- Features
-
- Complete situational Awareness across all layers of IT Security
- On-Demand Risk & Compliance Monitoring & Management
- Comprehensive security testing, flexible and on-demand
- Analytics Driven Identity Governance for and from Cloud
- Benefits
-
- Integrated & Modular - Best of both the worlds in terms of technology, infrastructure, industry standard processes & services bundled together at a cost which is affordable.
- Lower maintenance and higher flexibility - Nonlinear and simpler deployment option minimizing the time to market.
- High Availability - Proven processes and fully redundant that are available across geographically distributed data centers.
- Accelerated Productivity - You’ll stay compliant, reduce risk, and secure your devices and data without compromising employee productivity or privacy of your own or customer sensitive data.
- Faster Delivery & Immediate Protection - Instant provisioning over cloud, flexible provisioning and scaling, immediate services with minimal set up.