Introduction
Change is ‘inevitable’ in Technologies. New technologies will be arising every here and then. Few years ago, Internet of Things was the “Next big thing”. It had wide possibilities: millions of device objects were to be connected to the Internet and interconnected under the supervision of human beings. For enterprise, data accumulation and human supervision of those devices to improve people’s lives. But today the scenario has changed, the experts have started having concerns about technical, business and security approach from Internet of Things (IoT) to Identity of Things (IDoT). Regardless of whom you talk to, nobody denies that IDoT will be the next big “thing”.
The early adopters of Internet of Things (IoT) have left behind Identity and access management (IAM). Now, many big organizations are struggling to deal with the consequences. Any successful IoT implementations will have complex relationships to people, things, and services, and capable of sustaining and secure method for delivering operational value from device led solutions, is to enable firm Identity across all touch points and interactions.
As per the recent Gartner Research forecasts that over 20 billion IoT devices will be in use worldwide by 2020.
Why IoT requires IAM
IoT has reached a stage where consent and control over the devices and data is critical to the further success. The solution must offer a set of identity controls that properly govern who has access to what, when and why. In the identity world, these controls are the well-known concepts of authentication and authorization. In device-based identity management for IoT provides a range of benefits in the form of device management, predictive failure management, and automation.
Gartner predicts by 2020, more than 25 percent of identified attacks in enterprises will involve IoT, although IoT will account for less than 10 percent of IT security budgets.
Challenges and Impacts
- One of the challenges that identity Management Professionals is currently facing are able to manage the growing risks of IDoT and also to operate at a massive scale for IOT, which has to handle device registration, logins, authentications, session validation, device retirement etc. for millions of Identities. And whether to update our existing solutions or develop new solutions is another dilemma.
- The expansion of the IoT means the IAM leaders of digital businesses require a way of defining and managing the identities of “entities” (people, services and things) within a single platform.
- Just like Identity Lifecycle, a device lifecycle will include everything from device creation, updating and deletion also has to through device authentication and authorization. A common method is required to interact with those services and to increase integration time and reduce the cost of learning any new technology/platform.
- In the connected, smart and self-managed world, the very important risk will be around relationship of IoT which will make us look beyond IAM to include the level of relationship that exist among identities and their authorization for sharing data and making transactions.
- IoT devices gathers huge amounts of data. Users as well as regulators are concerned about how this data is being shared and used. In order to build trusted relationships with users and enable the sharing of valuable information (user history, type of data, preferences, etc.) that is key to delivering personalized experiences, privacy and policies must also be prioritized.
Few Examples to elaborate on the topic
The smart devices will not be in distant future to make transactions on behalf of their owners which must be controlled to manage risks including transaction repudiation.
A smart refrigerator will be enabled to make transactions/purchases through online without their owners being present based on the availability of food stored in it. How would business deal with validating the authenticity of the transactions and fight repudiation.
Solution Architecture
The traditional identity management can focus on Identities, but same attention has to be paid to all the entities making part of the system, then the approach changes drastically. It is no longer necessary to manage only the identity of a person connected to an application or asset, which is normally the case in IAM systems but also of a user connected to a device, two interconnected devices and an application. It is the new open, but secure ecosystem of the Identity of Things (IDoT), where all entities have the same interaction framework.
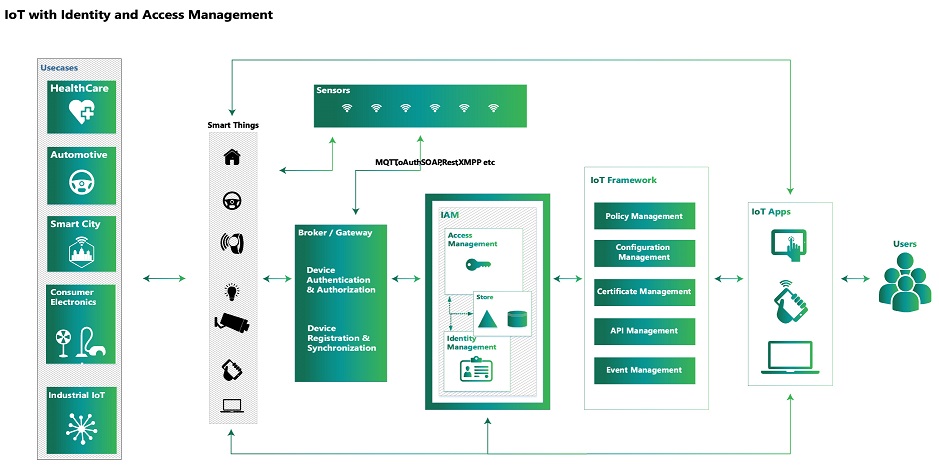
The Users try to communicate with the “Things” which includes security management which is composed of identity, access and right management. Users make use of IoT Applications to communicate with Smart Things which involves IoT Framework and as well as IAM Systems for authentication and authorization and also Identity Management to keep track of all devices like who has access to what, what sort of permission they have on devices etc.
Managing the Identity of Things (IDoT) involves assigning the unique identifiers to devices and things as well as authorization to communicate, share data, and transact. Every device will be assigned an identifier by IAM and it keeps track of who has access and how long the access he is required to have and also it revokes once the access is no longer required by a User. IoT Apps communicate with IoT Framework which includes Policy, API, Event Management etc. which in turn communicate with IAM System for various things including authentication and authorization. IAM in turn communicates with Gateway. The gateway is a device which is responsible for gathering data from sensors and communicating with other systems (like IAM Systems, Smart devices) when something needs to be controlled.
Once a collection of attributes has been defined and collected from a device, the attributes need to be stored during the device registration process. Few devices, registration may need some sort of unique verification to confirm that the device itself is legitimate. This is primarily important in the consumer IoT space, where connected items such as cars, sports apparel and equipment need to be protected from the threat of fake items. To eliminate the fake items, a simple approach could be to compare a value provided by the device to data held by the manufacturer of the device, such as a hard-coded unique identifier.
The Future
IAM for IoT should enable organizations to unify user identities, devices, and data in order to deliver consistent, personalized customer experiences on every channel to increase loyalty and revenue.
Current growth and requirements for IOT are focused on inter-operability and device connectivity. It seems the end result of increased connectivity and data collection is yet more data (metadata). From an operation standpoint, the data is used for predictive analytics and efficiency platforms, that can help to build a competitive edge. Data is what drives new revenue and business opportunities, whether the IoT solution is focused on customer service, automobile safety precautions, healthcare, energy efficiency or helping to develop autonomous machines.
We have begun to identify the risks and the identity management experts are working diligently to introduce solutions which addresses the risks. Evidently, Identity governance will be key to making sure that entities are able to communicate with one another and perform tasks which are approved and can be assigned ownership to a human identity for accountability purposes.

Arun is a former Happiest Mind and this content was created and published during his tenure.