

Agile is a very commonly used word in the world of software development. It has helped organisations drive better revenue through faster development, accomplish accuracy and achieve better time to market.

Cyber security is one of the most pressing challenges that global organizations are facing in this internet driven and interconnected IT business world.

Big Data Analytics is the process of collecting large chunks of structured/ unstructured data, segregating and analyzing it and discovering the patterns and other useful business insights from it.

NFV is an initiative to transfer the “Network Services” sector through virtualizing the network services by replacing the dedicated hardware with Virtual Machines

Unified Threat Management (UTM) represents a category of security features integrated into a centralized appliance which can be plugged into an organizational security hub. It consolidates all the disparate security points..

Bimodal IT is expected to act as a bridge that better connects the two worlds the traditional and advanced IT and lead us to a better enterprise environment which supports change management, scalability and high quality performance.
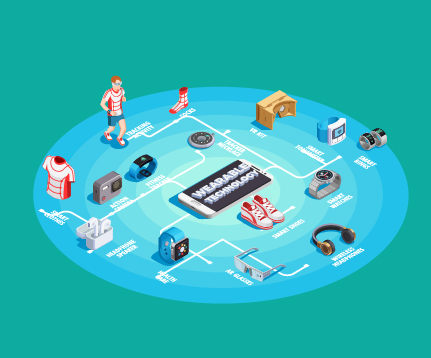
Wearables are electronic technology or devices incorporated into items that can be comfortably worn on a body. These wearable devices are used for tracking information on real time basis.

Retail in-store monitoring is a significant way of creating a much better retail in- store selling experience. It enables retailers in finding meaningful insights based on the analysis of data on customer........

In this age of advanced persistent threats, zero day attacks and advanced malware attacks, Threat intelligence is one of the key focus areas in the information security landscape...