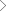Security can no longer be considered as an optional service, and when you embed security into the software development lifecycle (SDLC), you have applications that are safe and protected by design, not by accident or coincidence. A robust application security program will help enterprises build security into the application development lifecycle (SSDLC), develop security guidelines and standards, create awareness and security training, and execute effective application security assessments.
Happiest Minds enables organizations to develop meaningful security frameworks that arrest security flaws ahead in time, and generate insightful dashboards and metrics for all stakeholders—from executives to directors, program managers, and developers. The result is a development process that supports business goals and long-term initiatives while avoiding security oversights and pitfalls. At the same time, the framework provides the enterprise with comprehensive data to assist in complying with regulatory standards.
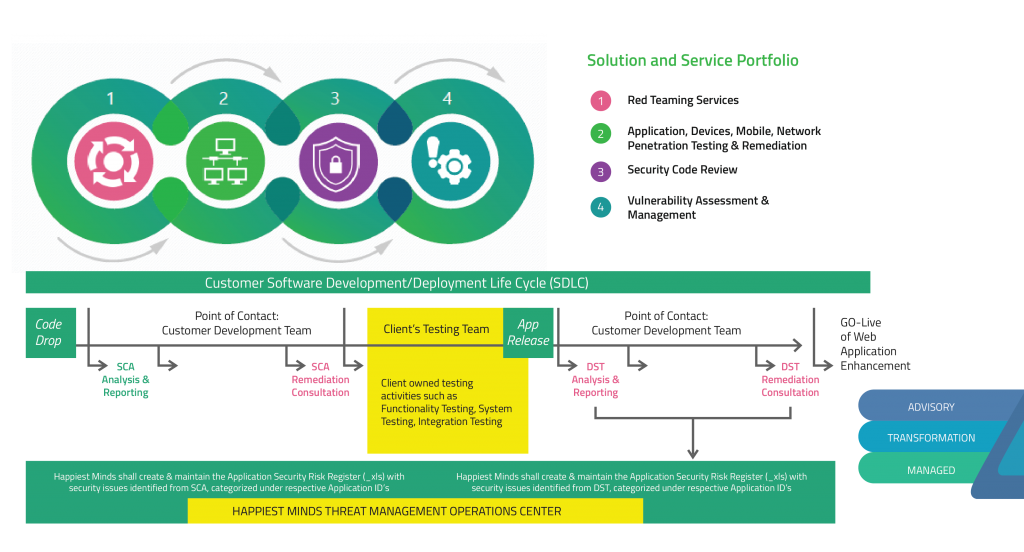
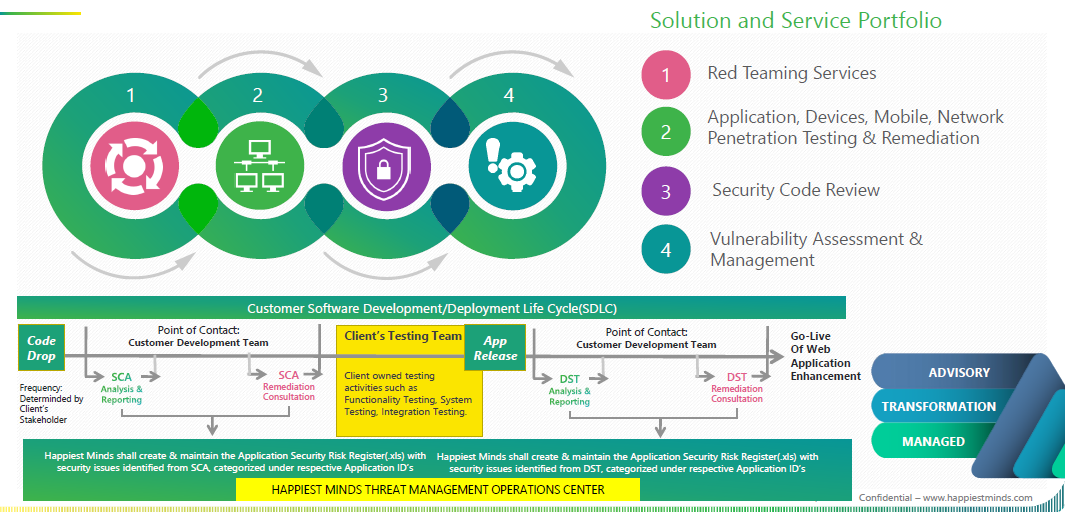
Happiest Minds’ advance threat management services follow industry standards such as OWASP, WASC, SANS, NIST. Our clients are able to leverage a hybrid model that integrates automatic scanning capabilities with manual testing. We proudly deliver the only end-to-end application threat management solution available in the market through our Application Security Operations Centers (ASOCs). The ASOCs cover security at different levels and are delivered via affordable pricing model options.
Why Happiest Minds?
Happiest Minds offers best-of-the-breed managed solutions to address multiple security needs, with flexible purchase options. Through our state-of-the-art center of excellence (COE) in Bangalore, India, and onsite and offsite delivery models, we offer tailored solutions to meet client requirements.
Our clients get a practical and powerful delivery roadmap, comprising a world-class delivery platform, framework, and standards. We possess the perfect mix of commercial and open-source tools and scripts. We use black box and grey box assessment methodologies, and follow a hybrid approach, maintaining a balance of tool-based and manual checks. We perform customized test cases focused on business logic. Our exhaustive checklist for test cases cover all possible attacks and vulnerabilities. We make use of the latest pentest enablement devices such as Hak5 – USB Rubber Ducky, LAN Turtle, and Tetra.
The ASOC packages encompass advanced threat management services across the software development lifecycle.
We leverage Threat Vigil 2.0, our cloud-based threat management solution for service delivery.