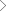ThreatVigil 2.0 – On Demand Threat Management & Remediation Solutions
As network infrastructure and threats continue to evolve, so too must the threat management security solutions to protect organizations. Your business needs a high-quality, scalable application testing solution that offers threat management, as well as both manual and automated testing approaches while being cost effective.
ThreatVigil 2.0 is one of the leading threat management solutions that offers an on-demand, cloud based, penetration testing platform, developed by Happiest Minds Technologies for various enterprise segments. With ThreatVigil 2.0 in place, IT has a threat management solution in place that protects vital information from new and vicious cyber-attacks. We understand that high-priced consulting and software solutions are not necessary for SMBs but they still need the assurance of secure applications and networks. Apart from affordable pricing, we offer unlimited testing of our sophisticated threat management solution for a year, which guarantees false positive elimination and business logic testing. Our ThreatVigil 2.0 also helps you cover the entire gamut of compliance requirements by ensuring business-critical information is secure and safe from threats.
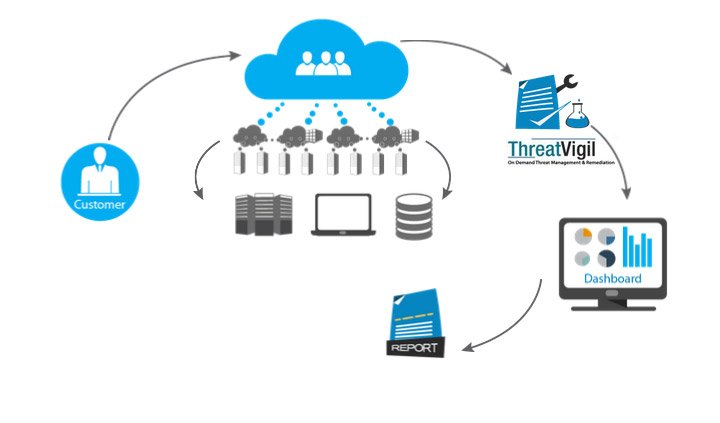
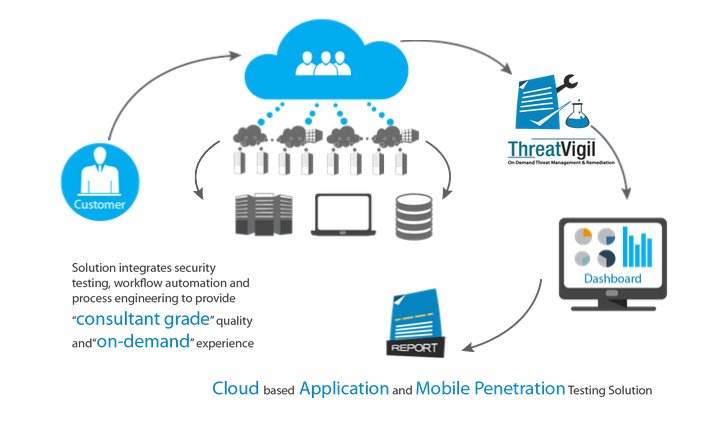
solution integrates security testing ,workflow automation and process engineering to provide “consultant grade” quality and “on-demand” experience
Cloud based Application and Mobile Penetration Testing solution
Why ThreatVigil?
Penetration Testing is the primary method for organizations to validate that its system does not have vulnerabilities that could expose it to potential attacks. This kind of testing solution identifies vulnerabilities in a system and proactively fixes them before attacks can be carried out. While there are a number of inexpensive, readily-available automated tools for penetration testing, these usually lack quality in threat management capabilities and set off a high number of false positives while missing business logic vulnerabilities. Further, security consultants are expensive and organizations will still need to buy the actual solution afterwards.
Clearly, the need of the hour is a high quality, scalable application testing solution that offers both manual and automated testing approaches while being cost effective. Our threat management solution comprises of a hybrid model that integrates automatic scanning capabilities with manual testing enables high quality results with an affordable pricing model. We offer the only threat management solution in the market that provides:
- End-to-end white box and black box testing
- Zero false positives
- Business logic testing
- Secure SDLC remediation
- Mobile penetration testing
Modules
- Network Penetration Testing
-
System & infrastructure network vulnerability assessment and penetration test is crucial to demystify the security exposures that are used to launch a cyber-attack through the internet. The security assessment of internet facing system or internal network test helps discover the vulnerable network services that can be exploited by unknown threat sources. The entire process is divided into five steps where identified security vulnerability is assessed thoroughly and reported along with appropriate recommendation or mitigation measures. The five phases are classified as:
- Phase 1- Profiling & Discovery
- Phase 2- Infrastructure Security Assessment
- Phase 3- Infrastructure Vulnerability Exploitation
- Phase 4- Reporting
- Phase 5- Remediation Consultation & Reassessment
- Application Penetration Testing
-
Application Penetration testing is executed using a blend of automated and manual technical security assessment approach to identify all the common vulnerabilities indicated by OWASP (Open Web Application Security Project) standard and all the other leading industry frameworks.
The application security assessment service offering covers web applications, web services and thick client applications. Web application security vulnerabilities are identified with automated tools and scripts along with manual assessment to eliminate false positives and negatives. From application profiling to the remediation approach, a detailed step by step approach is followed that tackles all application vulnerabilities.
- Phase 1- Application Profiling
- Phase 2- Automated Application Security Scanning
- Phase 3- Application Vulnerability Determination
- Phase 4- Application Vulnerability Exploitation
- Phase 5- Reporting
- Phase 6- Remediation Consultation & Reassessment
- Mobile Security Testing
-
Mobile native application penetration testing is executed using a blend of automated and manual technical security assessment approach to identify all the common vulnerabilities indicated by OWASP standard and all other leading industry frameworks. The mobile native application security assessment service offering covers installable applications on various mobile platforms such as Android, iOS, Windows and BlackBerry.
Mobile native application security vulnerabilities are identified with automated tools and scripts along with manual assessment to eliminate false positives and negatives. All exploitable security vulnerabilities in the target mobile native application are thoroughly assessed, recorded with associated risk ratings and reported to the client with an appropriate recommendation or mitigation measure. The stages involved in the entire mobile application penetration testing are:
- Phase 1- Mobile Application Profiling
- Phase 2- Automated Vulnerability Scanning
- Phase 3- Mobile Application Vulnerability Determination
- Phase 4- Mobile Application Vulnerability Exploitation
- Phase 5- Reporting
- Phase 6- Remediation Consultation & Reassessment