Keeping up with the ever-increasing, ever-changing threat landscape (in terms of volume and sophistication) is a major challenge for cybersecurity experts. The lack of expertise, resources, and processes to operationalize a threat detection and response program are some of the significant challenges that organizations face today. So, organizations must build a true security operation center (SOC) with 24*7 support from a dedicated team of experts who can continuously monitor suspicious behaviors and malicious activities with end-to-end management of threat hunting, detection, and response.
Happiest Minds’ Managed Detection & Response (MDR) services bring the combination of AI-powered threat monitoring and automated incident response capabilities backed by domain experts who can help you achieve 3x faster MTTD and MTTR round the clock.
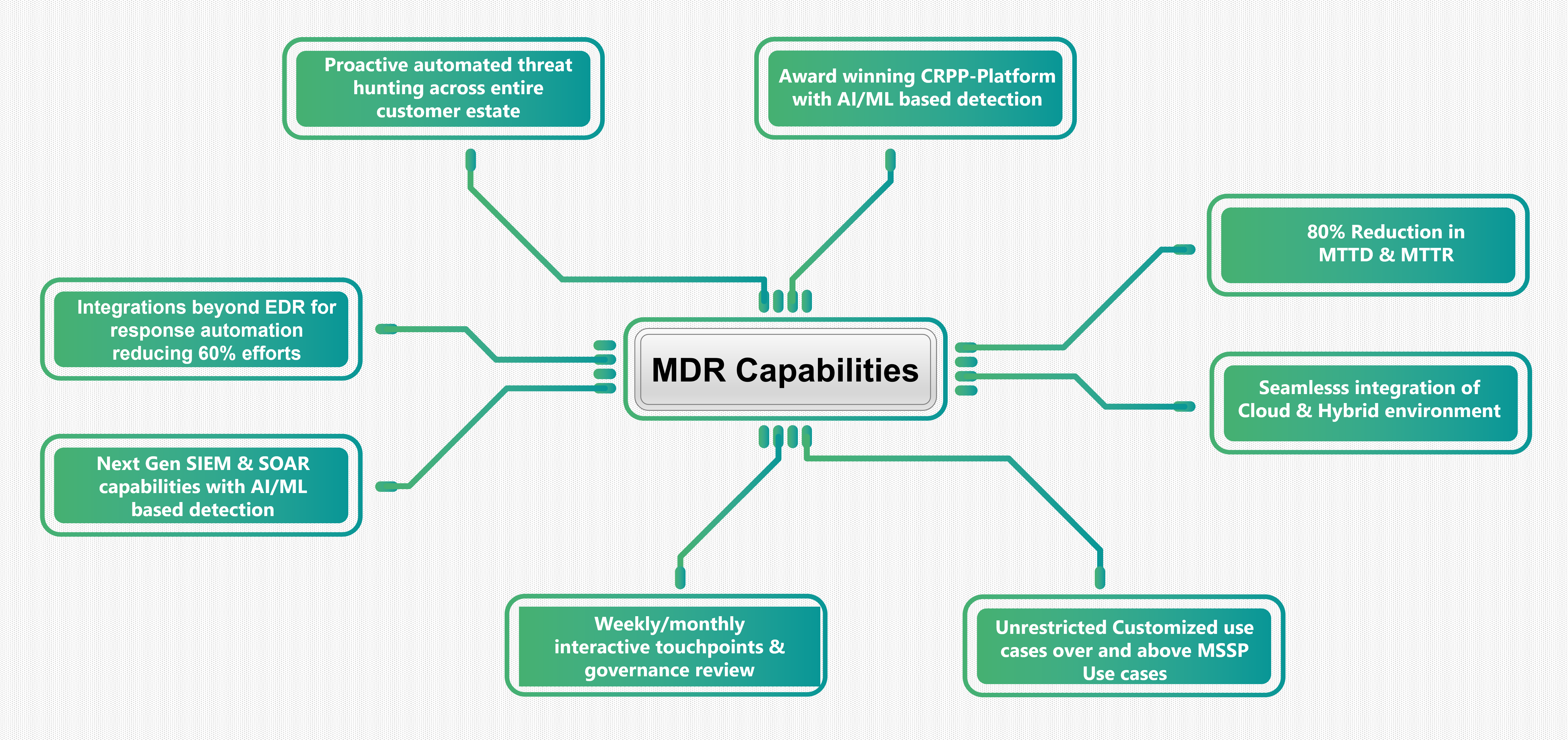
Our proactive security monitoring and incident response powered by AI and Analytics can be the right choice for your enterprise, enabling your organization with next-gen threat detection and response capabilities. Our MDR Portfolio is designed to offer multiple services to cover broader areas of the threat landscape of customers’ IT environment under one roof.