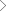The evolution of digital technology has fostered businesses to expand their presence globally much faster than ever before. The increased adoption of Cloud, SaaS, IoT, and more, has resulted in a widely distributed digital footprint. On the other hand, it has also become vulnerable to the increased threat landscape, which is more evasive, adaptive, perseverant, and targeted. Businesses need to build more comprehensive security strategies to tackle this, adopting next-generation detection and response methodologies to enable a secure digital expansion. This current scenario demands an integrated cyber risk management approach to tackling all cyber security risks and threats in cyberspace. Building an effective threat defense mechanism also means leveraging relevant analytics, cross-correlation across the vast security domains, and automation.
Happiest Minds, with its experience of supporting a wide range of customers, has developed its Cyber Risk Protection (CRPP) to efficiently address the challenges customers face in adapting to the ever-changing threat landscape.
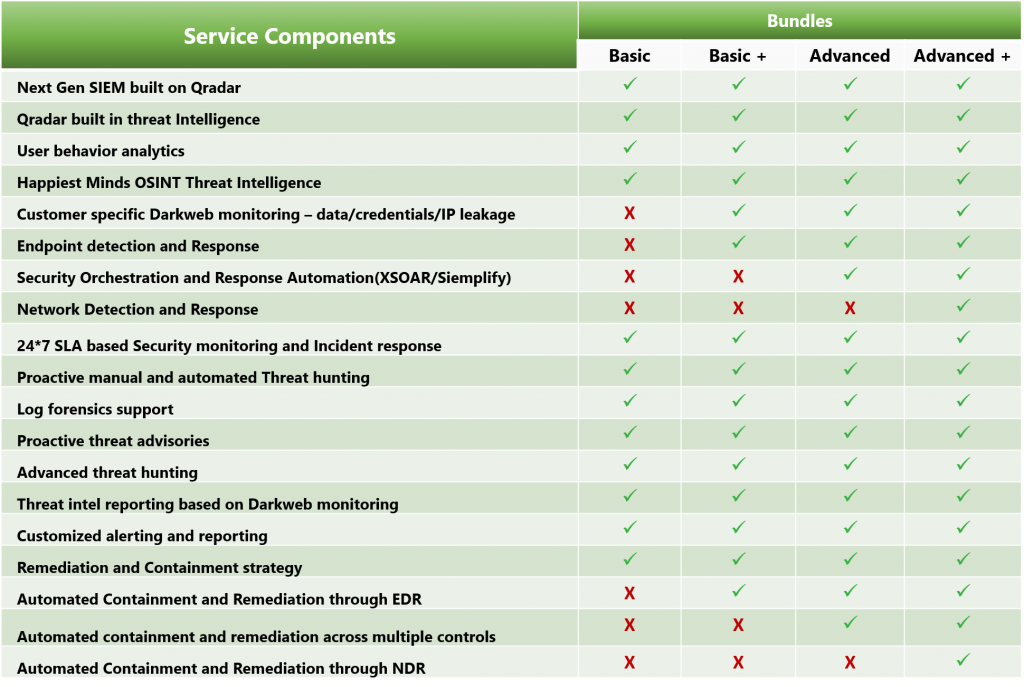
Our Next-Gen Cyber Risk Protection Platform (CRPP) Service
Cyber Risk Protection Platform (CRPP) is based on some of the best practices and essential data sources defined by Mitre att@ck, which contributes to effective detection of an attack that can engage different tactics and techniques in each attack phase. Our CRPP leverages multiple security technologies which have been leaders in their space for many years in the Gartner quadrant, such as IBM QRadar (Next gen SIEM), EDR, SOAR platforms, and more. These provide deeper analytics and insights for an integrated approach to handle the overall threat lifecycle and address cyber security risks holistically and stay ahead in the game.
Why CRPP?
Integrated threat detection and response across multiple layers of enterprise IT, removing siloed approach to security. An easy plug and play methodology to suite your business requirements.
Proactive
- Stay ahead with proactive Dark web monitoring for preempting a potential attack by early identification of possible weaponization against a company or its peers
- Global threat intelligence-based correlation to detect true positives, to channelize efforts in right direction
- Prioritize threats based on vulnerabilities you may be exposed to
- Proactive threat simulation to check effectiveness of security controls, detection tools and Security Incident response process
- Educate and strengthen the weak links of your organization through simulated phishing, vishing techniques
Adaptive
- Early adoption of Artificial Intelligence and Machine learning techniques to understand your environment and detect anomalies
- Leverage UEBA, EDR and NDR to bring that detection capabilities to profile systems , network traffic, users, and entities to detect Zero day and Advanced threats in your environment
Predictive
- Leverage the wide integration capability of our Next Gen SIEM built on Qradar which seamlessly integrates with On prem, cloud, SaaS, and Hybrid environments
- Wide list of two-way integration and actions through our SOAR platforms, for effective incident detection, response, containment, and remediation
- Well defined Mitre att@ck TTP based alert mapping for extended and accurate detection coverage
HAPPIEST MINDS 360-DEGREE APPROACH TO CRPP
- Consulting
-
Business requirement Assessment:
- Identify the business requirements and alignment.
- Evaluate solution fitment for customer expectations and reporting
Product Evaluation:
- Conducting proof of concept, evaluate solution fitment in customer environment.
- Custom connectors for unsupported devices for PoC
- PoC assessment and fitment report
Maturity Assessment:
- Assessment of existing configurations
- Assessment on the SOC process, its adherence and skill set levels
- Assessment report with recommendation
- Engineering Services
-
Solution Design:
- Technical architecture, design, and documentation
Implementation:
- Implementation of MDR tools – SIEM, EDR, SOAR, NDR etc.
- Data Sources integration and info fusion
- Custom Connector development
- Content development including dashboard, playbooks
- Use Cases activation, custom use case & automation use case development.
- Development of playbooks
- Customized Dashboards Creation
Gap assessments:
- Evaluate existing configurations
- Fine tuning and customization of use cases against best practice and environment mapping.
- Additional integrations and custom connectors development
- Customized dashboard, playbooks, automation and reporting development
- Managed Services
-
Services Rollout:
- Design, implementation, and integrations
Security Incident response:
- 24*7 SLA based monitoring and reporting
- Incident investigation and analysis
- Automated remediation, Remediation/containment recommendations and support
- Proactive threat hunting
- Daily, weekly, monthly, and quarterly reports
- Monthly and quarterly governance review
Platform engineering:
- Ongoing integrations and custom connector development
- Ongoing custom usecase and custom dashboard developments
- Ongoing playbook and Automation use case developments
- System upgrades and patching
- Packaged MDR as a Service
-