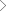The rapid acceleration of digital transformation has contributed to a rise in cybersecurity incidents. E-commerce, online banking, and the Internet of Things (IoT) are becoming a primary target for hackers to steal personal information, commit online theft, or commit malware attacks. According to the ENISA Threat Landscape report, cyberattacks are becoming more sophisticated, targeted, widespread, and undetected. Societies still have a long way to go before they can ensure that their digital environments are more secure. To combat the growing threats posed by digitalization and strengthen security requirements, enterprises need to address the following:
- Security of supply chains
- Streamline reporting obligations
- Introduce more stringent supervisory measures
- Stricter enforcement requirements
The new Network and Information Systems (NIS2) Directive will further strengthen the cybersecurity with reformed framework. In the long run, this will help more entities and sectors take the necessary steps to enhance their cybersecurity.
NIS Directive Objectives
National Cyber Security Centre (NCSC) Cyber Assessment Framework (CAF) further strengthens this directive implementation by providing a systematic and comprehensive approach to assessing the extent to which cyber risks to essential functions are being managed by the organization responsible.
CAF Objectives: