
Brochures

Over 80% of all Internet vulnerabilities are application related. Today commercially motivated or malicious hackers are crafting skillful attacks to penetrate unprotected sites for stealing information and destroying credibility.
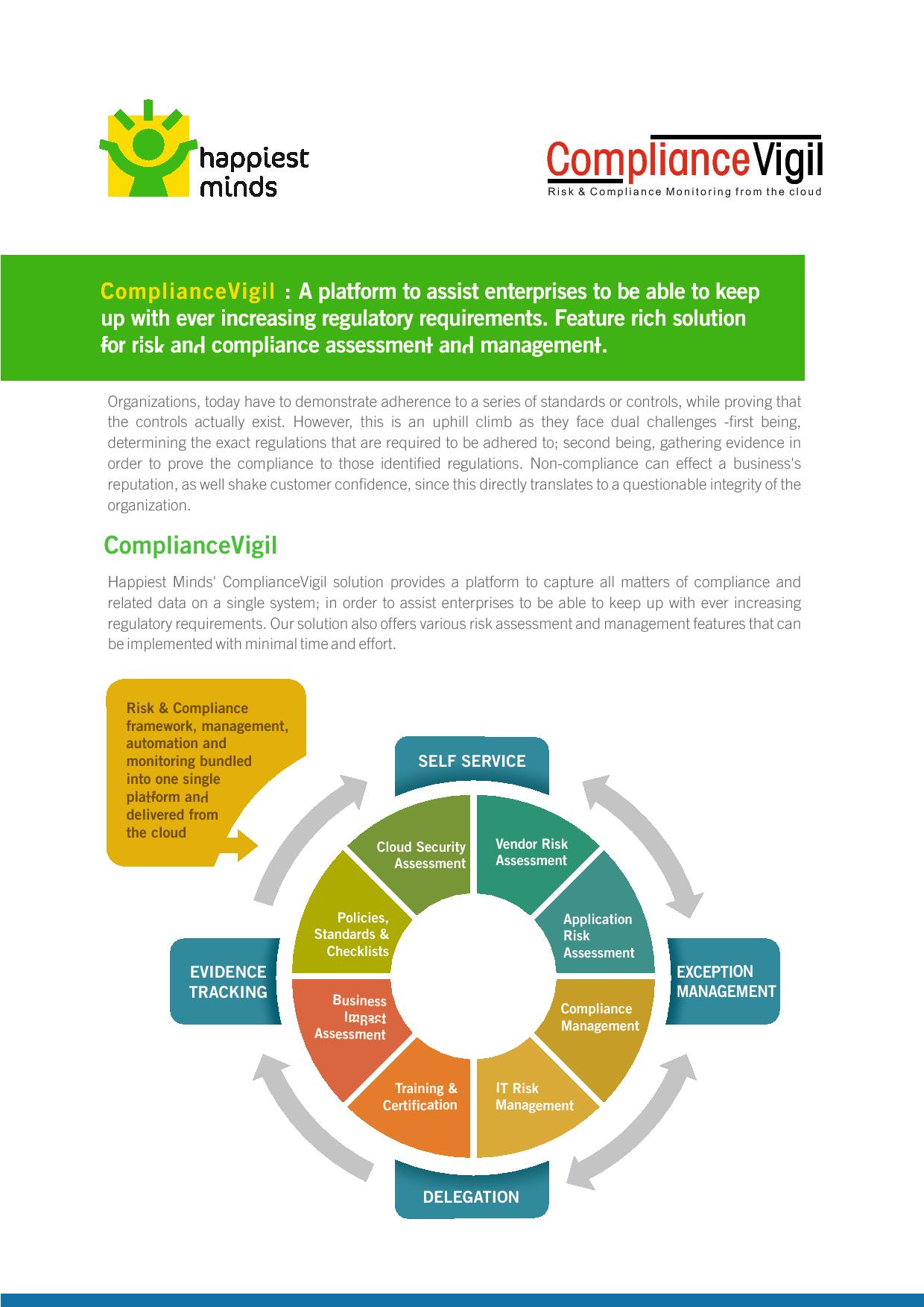
Organizations, today have to demonstrate adherence to a series of standards or controls, while proving that the controls actually exist. However, this is an uphill climb as they face dual challenges -first being, determining the exact regulations that are required…