Archives: Resource Centers
Alyne is a next-generation regTech, providing organisations with deep expertise and cutting edge technology to confidently navigate the increasingly complex world of Cyber Security, Governance, Risk Management and Compliance…
Offerings
- Services
-
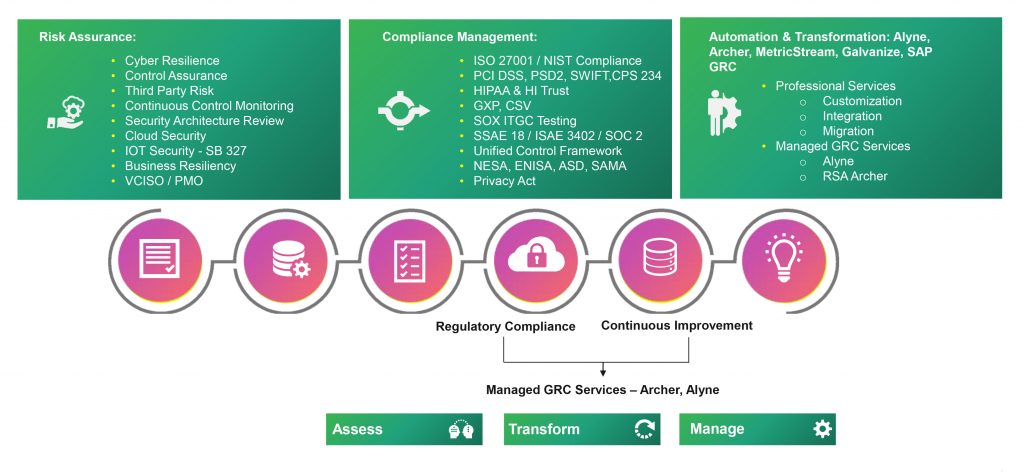
We at Happiest Minds have the experience and expertise to help our customers build an information risk office, or converge any existing information risk offices that might be working in silos or on fragmented/ad-hoc requirements today.
Our unique risk assessment framework not only ensures results that are realistic, but those that support ‘implementable’ remediation measures that are both repeatable and reusable.