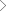Cyber security landscape in organizations are now witnessing highly organized, sophisticated and smart cyber-attacks as the digital world gets more connected. Addressing or reducing these cyber threats and attacks is a serious concern for Government, private sector players and law enforcement agencies, globally. The traditional security solutions and tools are insufficient for addressing these new age sophisticated cyber security attacks. Combining our deep expertise in Cyber security arena with Big Data Analytics capabilities, Happiest Minds brings in a Cyber Intelligence Platform, that is capable of, delivering automated real time alerts and notifications for organizations or governments regarding major cyber events or attacks, which can enable them to respond proactively.
The cloud based intelligence platform backed by a proficient team brings in timely and targeted high quality cyber intelligence solutions for addressing the ever changing cyber threats and protecting our clients’ critical business assets. Our turn key platform efficiently identifies and addresses a comprehensive range of cyber threats including DDoS attacks, data leakages, phishing attacks, data leakages, persistent attacks, password leakages, socially targeted attacks etc. Our efficient Big Data security team capture data, filter it, analyze it and convert it into actionable security insight that helps organizations in responding proactively to the potential cyber threats.
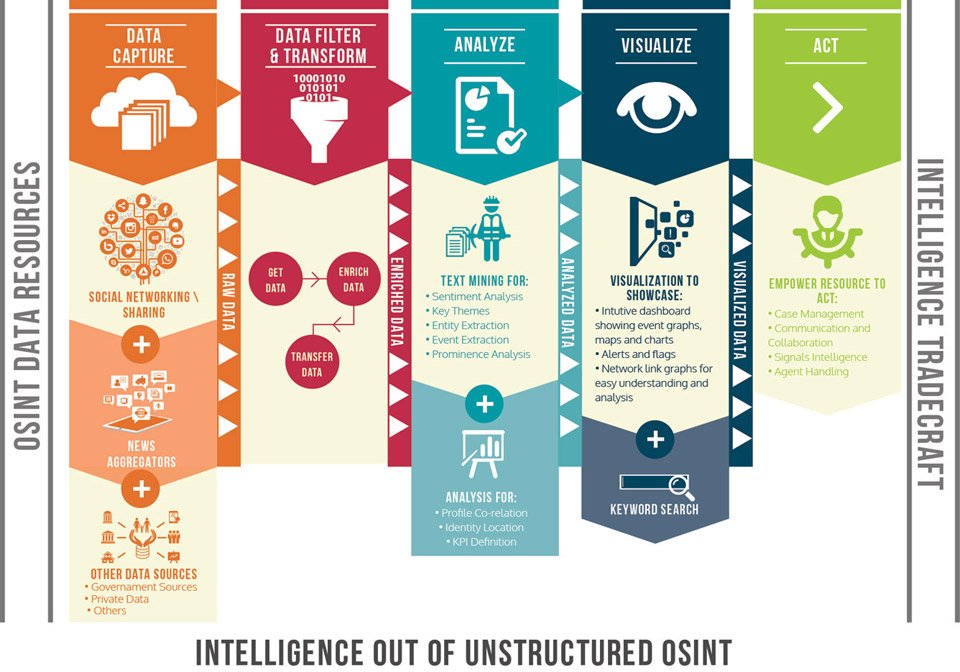
How it works?
The first step involves in capturing the raw data from multiple sources including social networking platforms, news aggregators, Government/ private sources etc. The advanced learning architecture of the system will analyze, filter and enrich the data and transfer it for further analysis. In this step the filtered and enriched data text will be made through sentimental analysis, entity extraction, event extraction and prominence analysis. The mined data will then be analyzed for Profile co relation, Identity location and KPI Definition. In the subsequent step the analyzed data will be visualized into intuitive dashboard showing event graph, maps and charts alerts and flags. Network line graphs will be also provided for easy understanding and analysis of the data. In the final actions step comes the empowerment of the resources to act by using Case Management, Communication and collaboration, Signals intelligence and Agent handling.
Our Solutions Differentiators
- A platform for real/near real time analysis of Big Data information leading to actionable insights
- Open source technology stack leading to lower total cost of ownership
- Contextual mining which in picking and analyzing only relevant content
- Powerful search feature to search for all related information in a single view
- Integration with facial recognition software to resolve social and national identity
- Option for integration with open deep web sources for mining text which is not available from general search engines
- Customized solutions backed by Cyber security specialists
Benefits
- Identify and Address potential cyber threats proactively
- Reduced risk of data leakage and subsequent damage to assets and reputation
- Mitigate the risks on time without causing more damage
- Efficiently identify internal data leakage is any
DATA CAPTURE
DATA FILTER
& TRANSFORM
ANALYZE
VISUALIZE
ACT
SOCIAL NETWORKING\
SHARING
TEXT MINING FOR:
- Sentiment Analysis
- Key Themes
- Entity Extraction
- Event Extraction
- Prominence Analysis
VISUALIZATION TO
SHOWCASE:
- Intuitive dashboard showing event graphs ,maps and charts
- Alerts and flags
- Network link graphs for easy understanding and analysis
EMPOWER RESOURCE TO
ACT
- Case Management
- Communication and Collaboration
- Signal Intelligence
- Agent Handling
NEWS \
AGGREGATORS
OTHER DATA SOURCES
- Government Sources
- Private data
- Others
ANALYSIS FOR:
- Profile Co-relation
- Identity Location
- KPI Definition
KEYWORD SEARCH
INTELLIGENCE OUT OF UNSTRUCTURED OSIANT
OSIANT DATA RESOURCES
RAW DATA
ENRICHED DATA
ANALYZED DATA
VISUALIZED DATA
INTELLIGENCE TRADECRAFT