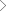“Information: Factual knowledge about something or someone. Interested acquirer uses some of the available resources to obtain this knowledge.”
This means that every information has a quantifiable value. With the paradigm shift from industrial to the digital era, most of the information is stored, processed, and shared digitally.
In addition to the cost of acquisition, the impacts of reputational losses entailing a data breach exponentially magnify the value of the information for enterprises, warranting diligent data protection, but its very nature imposes several challenges.
Nature
- Being distributable leads to the increased surface area, thereby increasing attack chances
- Its ‘omnipresent’ nature hides visibility and thereby reducing chances of being protected
Security is a balancing act- ‘A necessary evil’ 
“A system locked in an iron safe, guarded with gunmen outside, makes the system quite secured but defeats its very purpose”
- Security professionals struggle to make the act balancing with technology advancements
- Piecemeal implementations, product-oriented approach to protecting and lack of technology awareness add lesser value for money
DCLIP
A program structured to break the vicious cycle of balancing act alongside dealing with the agile nature of digital information.