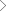We at Happiest Minds believe that Machine Learning and Artificial Intelligence driven Behavioral Analytics is the fulcrum for helping Predict, Prevent and Defeat cyberattacks in this age of increasing attacks/ threats like Advanced Persistent Threats. Cyber Analytics Platform from Happiest Minds is an enterprise grade security analytics and visualization platform focused on behavioral analytics of high velocity, real-time contextual enterprise data. Combining Big Data Technologies, Machine Learning and patented Algorithms, the Cyber Analytics platform helps discover insightful information and actionable cyber threat intelligence around security risks, targeted attacks and more.
• Excessive alerts and false positives from traditional SIEM tools
• Scalability of platforms as per business need without incurring significant capital expense
• Leverage existing investments for the transformation journey
• Finding out the “unknowns” that do not fit into known patterns
• Moving away from signature based or heuristics based tools
• Ability to process large volumes of data intelligence with high speed
• Bringing out the real-time threat posture
Why Cyber Risk Protection Platform (CRPP) with Next Generation Cyber Analytics?
CRPP with Cyber Analytics capabilities leverages Machine learning, Big Data, Trend Analysis, User Behavioral analysis (UBA), Entity Behavioral Analysis (EBA) and other techniques to identify anomalous behaviour, activities or trends of individual users, systems, and/or applications in an enterprise. The platform can monitor user accounts, end point devices and can be embedded in applications and networks in an organization. It combines the data collected from various network & end points to derive intelligent insights on the potential security risks in organizations that the cyber criminals may exploit. The self-learning platform continually adapts with repetitive usage and helps organizations build better security posture to defend the ever evolving cyber threat landscape.
The Cyber Analytics platform also helps enterprises address the current challenges with traditional security infrastructure and respond to the new age IT security requirements in a much more efficient way. This next generation CRPP Cyber Analytics platform works on a service based model enablling a smoother integration with traditional to advanced digital IT infrastructures, to meet clients’ next generation security needs.
The Cyber Analytics solution from Happiest Minds helps enterprises to instrument a portfolio of security management, automation, and orchestration; simultaneously enabling threat hunting and driving rapid Incident Response.
Combination of Cyber analytics with Third party SIEM
In successful UEBA deployments, the advantage comes from combining the specialized capabilities of UEBA with the broad visibility of SIEM. Successful overall incident management requires visibility and access to data and trends from throughout the SIEM architecture, which includes endpoint system and application data, threat intelligence, and asset profiles.
Integrating UEBA with third party SIEM provides a central point from which actions can take place—such as managing wide-ranging investigations, automating repetitious tasks, and remediating breaches
Enriching the UEBA with existing correlated data will give an efficient and effective Analysis of User and Entity behaviors
Use Cases
- User Behavior profiling
- External anomaly detection
- Internal fraud detection
- Network usage analytics
- Advanced alert triage and threat hunting
Features & Benefits
- Features
-
- User/ entity behavior profiling, segmentation and visualization
- High risk user/ entity identification, visualization and outlier detection
- Machine learning based anomaly detection in internal connections and assigning a risk score
- Data exfiltration and anomaly detection in external connections along with graphical representation of why an outlier led to an alert
- Advanced threat hunting capabilities an “exhaustive” & “fast” search capability to look for outliers / anomalies
- Data Analytics with extended user or entity intelligence covering Logon / log off events, AD events, Remote login patterns and Network usage
- Network analytics with reporting on Network band width usage, Connection count, DNS resolutions, to and fro Traffic from sources of bad reputation
- Analysing exclusive behavior patterns through machine learning and subsequent reduction false positives over a period of time
- Dynamic entity link analysis with User Mapping, Detection & highlighting hidden relationships between users, IP addresses, domain demonstration using Network Graph
- Reports and visualization using intuitive analytics dashboards, Compounded risk scores and Meta data with drill down capability on all reports
- Benefits
-
- Real-time detection upon occurrence of unusual activities
- Multidimensional understanding about users and analysts based on Machine learning.
- Artificial Intelligence: Disambiguation between Anomalous and Malicious behavior
- Searching & Hunting: Rich User Experience for Collaborative Discovery
- Reinforcement learning to automate Kill-Chain mapping and to distinguish malicious from anomalous.
- Signature-less behavior based analytics for detecting insider and targeted cyber attacks
- User and entity centric monitoring across hosts, network and applications